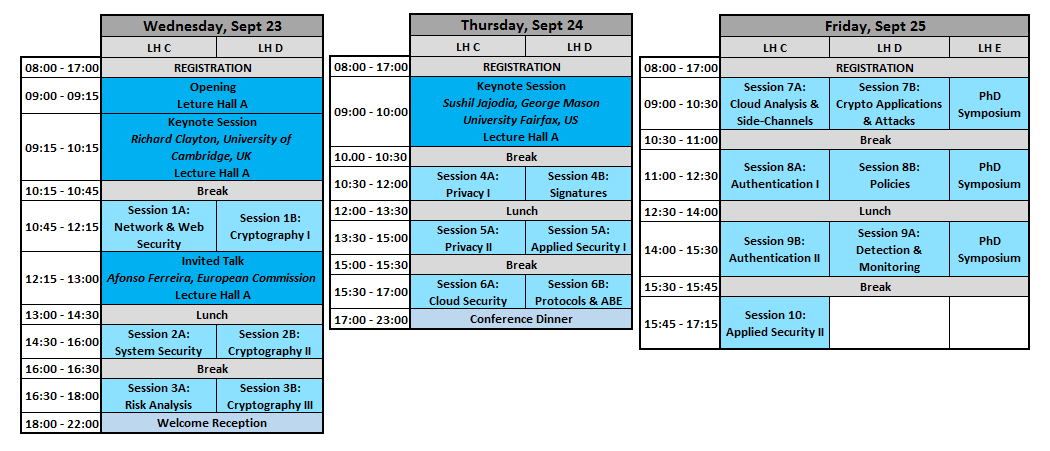
Program Overview ESORICS 2015:
Download the Program Guide ESORICS 2015
Program ESORICS 2015:
| Wednesday, September 23 | |||
| 09:00-09:15 | Opening | ||
| 09:15-10:15 | Keynote Session | ||
| Cybercrime data: Big, Biased and Beyond Review? Richard Clayton, University of Cambridge, UK: |
|||
| 10:15-10:45 | Coffee Break | ||
| 10:30-12:00 | Session 1A: Network & Web Security | ||
| Haya Shulman and Michael Waidner. DNS-Scopy: Towards Security of Internet Naming Infrastructure | |||
| Joerg Schwenk, Mario Heiderich and Marcus Niemietz. Waiting for CSP — Securing Legacy Web Applications with JSAgents | |||
| Daniel Fett, Ralf Kuesters and Guido Schmitz. Analyzing the BrowserID SSO System with Primary Identity Providers Using an Expressive Model of the Web | |||
| 10:45-12:15 | Session 1B: Cryptography I | ||
| Michael Backes, Esfandiar Mohammadi and Tim Ruffing. Computational Soundness for Interactive Primitives | |||
| Fabrice Benhamouda, Stephan Krenn, Vadim Lyubashevsky and Krzysztof Pietrzak. Efficient Zero-Knowledge Proofs for Commitments from Learning With Errors over Rings | |||
| Gildas Avoine, Xavier Carpent and Cédric Lauradoux. Interleaving Cryptanalytic Time-memory Trade-offs on Non-Uniform Distributions | |||
| 12:15 – 13:00 | Invited talk | ||
| The European Strategic Agenda for Research and Innovation in Cybersecurity Afonso Ferreira, European Commission: |
|||
| 13:00-14:30 | Lunch | ||
| 14:30-16:00 | Session 2A: System Security | ||
| Ping Chen, Jun Xu, Zhiqiang Lin, Dongyan Xu, Bing Mao and Peng Liu. A Practical Approach for Adaptive Data Structure Layout Randomization | |||
| Hind Chfouka, Hamed Nemati, Roberto Guanciale, Mads Dam and Patrik Ekdahl. Trustworthy prevention of code injection in Linux on embedded devices | |||
| Daniel Gruss, David Bidner and Stefan Mangard. Practical Memory Deduplication Attacks in Sandboxed Javascript | |||
| 14:30-16:00 | Session 2B: Cryptography II | ||
| Kazuhiko Minematsu. Efficient Message Authentication Codes with Combinatorial Group Testing | |||
| Chaowen Guan, Kui Ren, Fangguo Zhang, Florian Kerschbaum and Jia Yu. A Symmetric-Key Based Proofs of Retrievability Supporting Public Verification | |||
| Oscar Garcia-Morchon, Ronald Rietman, Sahil Sharma, Ludo Tolhuizen and Jose-Luis Torre-Arce. DTLS-HIMMO: Achieving DTLS certificate security with symmetric key overhead | |||
| 16:00-16:30 | Coffee Break | ||
| 16:30-18:00 | Session 3A: Risk Analysis | ||
| Aron Laszka and Jens Grossklags. Should Cyber-Insurance Providers Invest in Software Security? | |||
| Jan Tobias Muehlberg, Job Noorman and Frank Piessens. Lightweight and Flexible Trust Assessment Modules for the Internet of Things | |||
| Paul Beaumont, Neil Evans, Michael Huth and Tom Plant. Confidence analysis for nuclear arms control: SMT abstractions of Bayesian Belief Networks | |||
| 16:30-18:00 | Session 3B: Cryptography III | ||
| Tibor Jager, Jörg Schwenk and Juraj Somorovsky. Practical Invalid Curve Attacks on TLS-ECDH | |||
| Aggelos Kiayias and Qiang Tang. Making any Identity Based Encryption Accountable, Efficiently | |||
| Jonathan Bootle, Andrea Cerulli, Pyrros Chaidos, Essam Ghadafi, Jens Groth and Christophe Petit. Short Accountable Ring Signatures Based on DDH | |||
| 18:00-22:00 | Welcome Reception | ||
| Thursday, September 24 | |||
| 09:00-10:00 | Keynote Session | ||
| Adversarial and Uncertain Reasoning for Adaptive Cyber Defense: Building the Scientific Foundation Sushil Jajodia, George Mason University Fairfax, US |
|||
| 10:00-10:30 | Coffee Break | ||
| 10:30-12:00 | Session 4A: Privacy I | ||
| Christof Torres, Hugo Jonker and Sjouke Mauw. FP-Block : usable web privacy by controlling browser fingerprinting. FP-Block Firefox plugin for downloading! | |||
| Wenrui Diao, Xiangyu Liu, Zhe Zhou, Kehuan Zhang and Zhou Li. Mind-Reading: Privacy Attacks Exploiting Cross-App KeyEvent Injections | |||
| Xingliang Yuan, Helei Cui, Xinyu Wang and Cong Wang. Enabling Privacy-assured Similarity Retrieval over Millions of Encrypted Records | |||
| 10:30-12:00 | Session 4B: Signatures | ||
| Christian Hanser, Max Rabkin and Dominique Schröder. Verifiably Encrypted Signatures: Security Revisited and a New Construction | |||
| Rupeng Yang, Qiuliang Xu, Yongbin Zhou, Rui Zhang, Chengyu Hu and Zuoxia Yu. Updatable Hash Proof System and Its Applications | |||
| Baodong Qin, Robert Deng, Yingjiu Li and Shengli Liu. Server-Aided Revocable Identity-Based Encryption | |||
| 12:00-13:30 | Lunch | ||
| 13:30-15:00 | Session 5A: Privacy II | ||
| Yao Zheng, Bing Wang, Wenjing Lou and Y. Thomas Hou. Privacy-Preserving Link Prediction in Decentralized Online Social Networks | |||
| Florian Kerschbaum and Hoon Wei Lim. Privacy-Preserving Observation in Public Spaces | |||
| Qiang Tang and Jun Wang. Privacy-preserving Context-aware Recommender Systems: Analysis and New Solutions | |||
| 13:30-15:00 | Session 5B: Applied Security I | ||
| Behnaz Hassanshahi, Yaoqi Jia, Roland Yap, Prateek Saxena and Zhenkai Liang. Web-to-Application Injection Attacks on Android: Characterization and Detection | |||
| Raja Naeem Akram, Konstantinos Markantonakis and Keith Mayes. Enhancing Java Runtime Environment for Smart Cards Against Runtime Attacks | |||
| Christian Decker, James Guthrie, Jochen Seidel and Roger Wattenhofer. Making Bitcoin Exchanges Transparent | |||
| 15:00-15:30 | Coffee Break | ||
| 15:30-17:00 | Session 6A: Cloud Security | ||
| Sky Faber, Stanislaw Jarecki, Hugo Krawczyk, Quan Nguyen, Marcel C. Rosu and Michael Steiner. Rich Queries on Encrypted Data: Beyond Exact Matches | |||
| Yanjiang Yang, Joseph Liu, Kaitai Liang, Raymond Choo and Jianying Zhou. Extended Proxy-Assisted Approach: Achieving Revocable Fine-Grained Cloud Data Encryption | |||
| Liang Feng Zhang and Reihaneh Safavi-Naini. Batch Verifiable Computation of Polynomials on Outsourced Data | |||
| Qian Wang, Shengshan Hu, Kui Ren, Meiqi He, Minxin Du and Zhibo Wang. CloudBI: Practical Privacy-Preserving Outsourcing of Biometric Identification in the Cloud | |||
| 15:30-17:00 | Session 6B: Protocols & Attribute-based encryption | ||
| Omar Almousa, Sebastian A. Mödersheim, Paolo Modesti and Luca Viganò. Typing and Compositionality for Security Protocols: A Generalization to the Geometric Fragment | |||
| Rémy Chrétien, Veronique Cortier and Stephanie Delaune. Checking trace equivalence: How to get rid of nonces? | |||
| Tran Viet Xuan Phuong, Guomin Yang and Willy Susilo. Attribute Based Broadcast Encryption with Short Ciphertext and Decryption Key | |||
| Jianting Ning, Xiaolei Dong, Zhenfu Cao and Lifei Wei. Accountable Authority Ciphertext-Policy Attribute-Based Encryption with White-Box Traceability and Public Auditing in the Cloud | |||
| 17:00-23:00 | Conference Dinner | ||
| Friday, September 25 | |||
| 09:00-10:30 | Session 7A: Code Analysis & Side-Channels | ||
| Yueqian Zhang, Xiapu Luo and Haoyang Yin. DexHunter: Toward Extracting Hidden Code from Packed Android Applications | |||
| Hong Hu, Zheng Leong Chua, Zhenkai Liang and Prateek Saxena. Identifying Arbitrary Memory Access Vulnerabilities in Privilege-Separated Software | |||
| Wei Wang, Jingqiang Lin, Zhan Wang, Ze Wang and Luning Xia. vBox: Proactively Establishing Secure Channels between Wireless Devices without Prior Knowledge | |||
| 09:00-10:30 | Session 7B: Crypto Applications & Attacks | ||
| Alessandro Barenghi, Alessandro Di Federico, Gerardo Pelosi and Stefano Sanfilippo. Challenging the Trustworthyness of PGP: Is the Web-of-Trust Tear-proof? | |||
| Heiko Mantel and Artem Starostin. Transforming Out Timing Leaks, More or Less | |||
| Junrong Liu, Yu Yu, Francois-Xavier Standaert, Zheng Guo, Dawu Gu, Wei Sun, Yijie Ge, Rong Fu and Xinjun Xie. Small Tweaks do Not Help: Differential Power Analysis of MILENAGE Implementations in 3G/4G USIM Cards | |||
| 09:00-10:30 | PhD Symposium – Session 1 | ||
| Ivan Homoliak. Improvement of Network Intrusion Detection Using Various Obfuscation Techniques | |||
| Rodrigo Carvalho. Semantic technologies applied to digital forensics analysis and evidence modelling | |||
| Dominik Breitenbacher. Technology Analysis of IDS and NBA systems from the view of detection effectivity | |||
| 10:30-11:00 | Coffee Break | ||
| 11:00-12:30 | Session 8A: Authentication I | ||
| Swee-Won Lo, Zhuo Wei, Robert Deng and Xuhua Ding. On Security of Content-based Video Stream Authentication | |||
| Marina Blanton and Siddharth Saraph. Oblivious Maximum Bipartite Matching Size Algorithm with Applications to Secure Fingerprint Identification | |||
| Xun Yi, Feng Hao, Liqun Chen and Joseph Liu. Practical Threshold Password-Authenticated Secret Sharing Protocol | |||
| 11:00-12:30 | Session 8B: Policies | ||
| Donald Ray and Jay Ligatti. A Theory of Gray Security Policies | |||
| Ximeng Li, Flemming Nielson and Hanne Riis Nielson. Factorization of Behavioral Integrity | |||
| Kristopher Micinski, Jonathan Fetter-Degges, Jinseong Jeon, Jeffrey Foster and Michael Clarkson. Checking Interaction-Based Declassification Policies for Android Using Symbolic Execution | |||
| 11:00-12:30 | PhD Symposium – Session 2 | ||
| Sune K. Jakobsen. Cryptogenography | |||
| Jens Lindemann. Detecting and Preventing Abuse of Resources in IaaS Cloud Computing | |||
| Patrick McCorry. Why the Bitcoin Community needs to pursue Bitcoin-based Authentication | |||
| 12:30-14:00 | Lunch | ||
| 14:00-15:30 | Session 9A: Authentication II | ||
| Jingyu Hua, Shaoyong Du and Sheng Zhong. Towards Attack-Resistant Peer-Assisted Indoor Localization | |||
| Mahdi Nasrullah Al-Ameen, Kanis Fatema, Matthew Wright and Shannon Scielzo. Leveraging Real-Life Facts to Make Random Passwords More Memorable | |||
| Ding Wang and Ping Wang. The Emperor’s New Password Creation Policies | |||
| 14:00-15:30 | Session 9B: Detection & Monitoring | ||
| Sufatrio, Tong-Wei Chua, Darell J. J. Tan and Vrizlynn L. L. Thing. Accurate Specification for Robust Detection of Malicious Behavior in Mobile Environments | |||
| Maximilian Seitzer, Michael Gruhn and Tilo Müller. A Bytecode Interpreter for Secure Program Execution in Untrusted Main Memory | |||
| Youngja Park, Ian Molloy, Suresh Chari, Zenglin Xu, Chris Gates and Ninghui Li. Learning from Others: User Anomaly Detection Using Anomalous Samples from Other Users | |||
| 14:00-15:30 | PhD Symposium – Session 3 | ||
| Eric Rothstein Morris. A Coinductive System Calculus for Security Properties | |||
| Christian Sillaber. Data Quality Management in Information Systems Security Documentation | |||
| Zhioua Zeineb. Formal specifica6on and verificaton of Security guidelines, Derivation of Security properes using static code analysis. | |||
| 15:30-15:45 | Coffee Break | ||
| 15:45-17:15 | Session 10: Applied Security II | ||
| Dibya Mukhopadhyay, Maliheh Shirvanian and Nitesh Saxena. All Your Voices Are Belong to Us: Stealing Voices to Fool Humans and Machines | |||
| Tobias Pulls and Roel Peeters. Balloon: A Forward-Secure Append-Only Persistent Authenticated Data Structure | |||
| Léa Samarji, Nora Cuppens-Boulahia, Frédéric Cuppens, Serge Papillon, Waël Kanoun and Samuel Dubus. On the Fly Design and Co-simulation of Responses against Simultaneous Attacks | |||